Hands-on Lab Platform
Empowering learning and enablement through modern immersive technology experiences.



Impactful Learning Experiences
Proven For Scale
Increased Market Outreach
Our Mission
Enable immersive content experiences that allow consistent and seamless engagement between content creators and customers through a virtual training platform, an online hands-on learning environment.
CloudLabs Services
CloudLabs is designed for organizations and educational institutes of all sizes to offer an impactful learning experience with zero to minimal management overhead.
HOL Platform
Demos
Modernize Education
Event & Hackathons
LMS Integration
Skill Validation
Content Development
Diverse Lab Catalogue
Adding Impact to Virtual trainings
CloudLabs is built from ground up to support virtual learning through technologies.
We can help with enabling your learning and development programs in Covid Era.

CloudLabs reinvents the way how technology experiences are delivered
Proven Lab Platform
CloudLabs is trusted by organizations and educational institutes worldwide+0
Labs Provisioned
+0
Trained Participants
+0
Events Supported
Some of our Clients











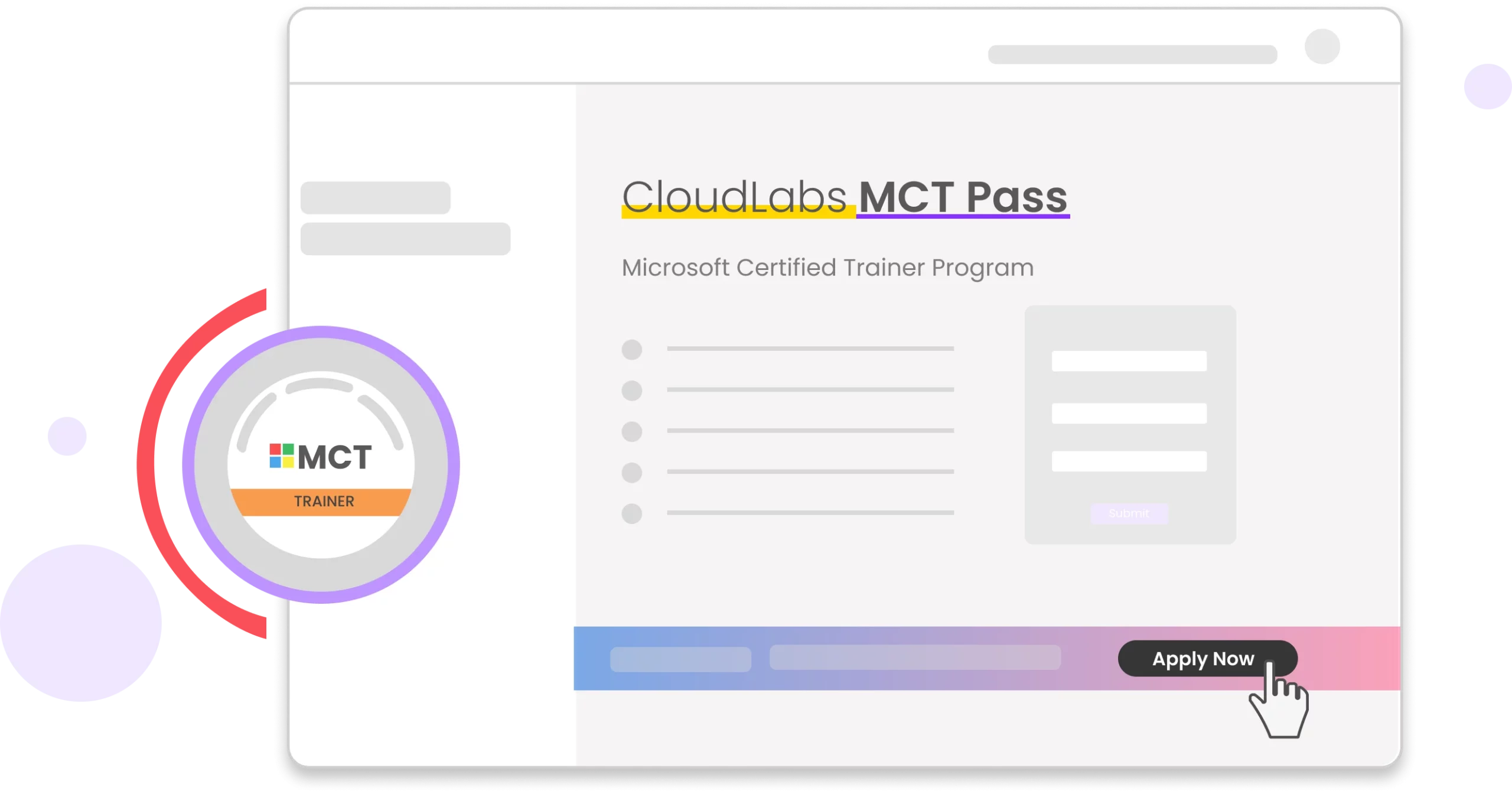
CloudLabs for MCTs
With CloudLabs MCT Pass, MCTs can now enjoy CloudLabs platform to prepare for their upcoming trainings and certifications exams.
MCT Pass is designed to help instructors get familiar with platform and be ready to deliver impactful trainings with powerful HOLs & Practice Tests.



Reduce Labs Costs up to 80%
CloudLabs platform leverages the public cloud platforms to host labs in a cost effective fashion, which can work for organizations of every size.
Latest Topics. Articles. Tutorials.
Exclusively for you!
Articles from specialists to keep you updated with the latest news & our learning of running Labs at scale.
Strong Cost Controls
Track your Cloud Spend
Eliminate Silos
Got Questions? Reach Us
Talk to us today for a live platform Demo and get your questions answered.
Impactful learning experiecnes are a demo booking away 🙂

 CloudEvents
CloudEvents